In English, please: Verizon’s Data Breach Report Explained by a Cyber Security Engineer.
- Andrew Fedkovich

- Sep 19, 2024
- 6 min read
Andrew Fedkovich's Take on 2024 Verizon Data Breach Report.

The 2024 Data Breach Investigations Report by Verizon highlights significant trends in cybersecurity breaches. How exactly do those breaches occur? If you know the reason, you’re halfway there to beat the root of the cause and hence ensure the safety of your business.
Hi, I’m Andrew Fedkovich, Cyber Security Developer at Identité®, and today I’ll share with you my understanding of Verizon's report. In plain English, so that you could clearly understand the causes of the problem and what you can do about it.
The timeline of the Data Breach Report and how to use this comment
Verizon’s message opens the report with the details on the 2024 DBIR incident dataset and the rules of citing.

Thus, my comment is in no way paraphrasing the contents of Verizon Data Breach Report 2024. Rather, it’s an attempt to make it clearer for people not familiar with the industry’s terminology, but eager to understand the modern threat environment.
Breaches involving credentials are the most common type of incidents reported.
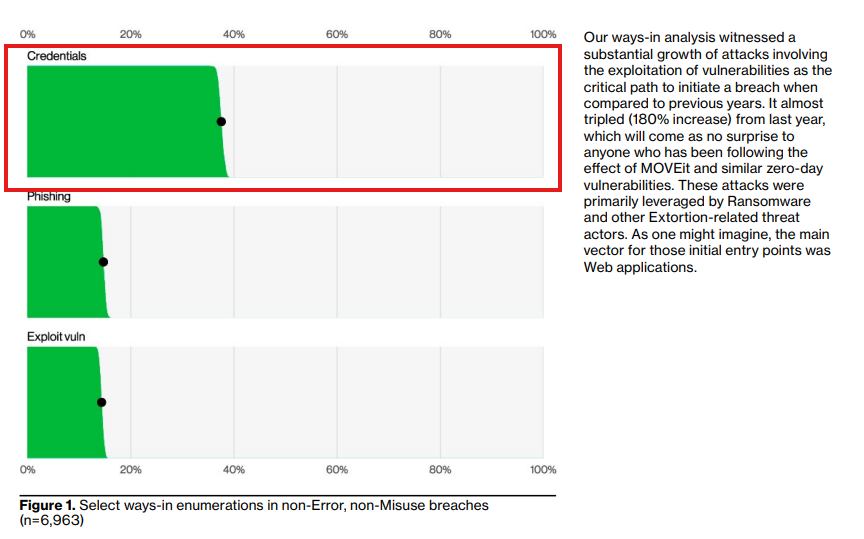
Verizon's DBIR 2024, Page 7
Breaches involving credentials open up the Summary of Findings (Page 7 of the report). What does this chart mean for a statistical average of Internet users?
To access most online resources—whether web applications or mobile apps—users must authenticate their identity, typically through credentials like a username and password or access tokens. When these credentials are leaked or stolen, unauthorized users can exploit them to breach systems. This is where the real risk lies and how most breaches occur.
How to address the problem of credential loss or unauthorized access?
Spoiler alert: Passwordless MFA.
Think of it this way: If there's nothing to steal, you cannot lose it. The same applies to credentials. If they don't exist, but the system still allows users to authenticate securely, the risk of stolen credentials is eliminated, thus reducing the likelihood of these issues.
The idea behind solutions like NoPass™ — which our team is working on is simple: employees no longer need to remember a variety of passwords for different systems, enhancing security and productivity by removing the possibility of password theft.
For Consumers, we offer PasswordFree®, which was built on the same common foundation of Full Duplex Authentication®. This is a patented technology designed to address the escalating threats of phishing, browser-in-browser and rogue proxy attacks.

We propose to use a secure mobile app instead of a plain text doc, email, or sticky note.
Here are the quick stats on where users generally store their passwords, if not in a password manager or a special secure mobile application (according to the Public Poll on Spiceworks):
Ridiculous places that users store passwords? (Several options allowed)
56% of users keep new passwords on the monitor
41% of users keep their passwords under the keyboard
37% of users save them in a text file or spreadsheet on their desktop.
So, it's safe to say that far from everyone in your company stores their passwords in highly secure or protected locations.
A NoPass™ user has a mobile app that acts as a key to access multiple applications. This means they don't need to store various passwords in an oftentimes insecure manner.
Avoid common password patterns – hackers know them all.
Studies have shown that common passwords often consist of simple number combinations or include some easy to remember tokens – the name of a favorite football club, a pet’s name, or your spouse’s phone number.

Inspired by: Reddit
Hackers who try to breach accounts are aware of these studies and use them to guess passwords by generating likely combinations.

Source: Most Common Passwords 2024
If there’s no password, it can’t be guessed. NoPass™, PasswordFree®, and similar Passwordless MFA solutions are designed specifically to eliminate the need for passwords. Instead, you use a Passwordless MFA mobile app (here’s one for Apple users) to store your access keys.
For example, the NoPass™ Employee Single-Sign-On solution makes it easy for employees to access applications with secure and easy login procedure. To authenticate, all they need to do is match two images—a picture and a 3-digit code in their mobile app and on their desktop—and then hit the "Approve" button, if those match.
The system also offers extra security through options like hardware tokens (such as Yubikeys) or biometric verification, including face recognition or fingerprints. This technology is patented and meets NIST 800-63-B AAL3 standards, ensuring the highest level of security.

How NoPass™ Employee Single-Sign-On solution works
Watch a short YouTube video for a 2-min demo on safe Passwordless authentication.
If data is sent to a server, it means that data can potentially be intercepted.
Last but not least, any communication between a browser on a computer and a server involves the transfer of user input from the browser to the server. Therefore, if a password is entered somewhere, it can be intercepted in various ways during its journey from the user's browser to the target server.
This is a basic explanation of why Passwordless MFA is a way to go in today’s cybersecurity environment — it eliminates the need to enter passwords altogether.
Does Passwordless MFA protect users against phishing attacks?

Verizon's DBIR 2024, Page 7
The short answer is: Partially. (Not all MFA methods will protect you against phishing, unless you’re using a phishing-resistant MFA – the one that we provide using our Full Duplex Authentication®).
Although Verizon categorizes phishing separately (and those account for almost 20% of all security incidents), this type of attack is closely related to credential breaches.
By the way, Verizon also provides data on how many users click on phishing links, and even in simulations, the numbers are quite alarming.

Verizon's DBIR 2024, Page 9
How does NoPass™ help in combating phishing attacks?
In simple terms, phishing refers to the practice of sending a fraudulent email or SMS purporting to be from a reputable organization to solicit passwords, OTPs, and other personal information. Hundreds of millions of emails or SMS texts can be sent and if this results in as few as 1 compromised account, the campaign is a success. That’s why emails and SMS phishing are often on top of the charts of data breach examples.
Note that passwords and SMS OTP’s, which is a common practice for MFA, can easily be phished. Read more about why SMS shouldn’t be used for MFA here.
If you check your spam folder, you’ll likely find numerous such messages with links. These attackers obtain users' email addresses and send out messages with harmful links. By clicking on one, the user might end up on a scam site that looks like a legitimate one but differs by a small character, which a regular user might not notice. On such sites (see a short list of types of scam websites in the picture below), the user is often asked to either make a payment or log in by entering their credentials.

When this phishing message is sent to many people, some will be more cautious, set up proper filters, and avoid clicking on the link.
Others may click the link but not enter any information.
However, there is always a percentage who will proceed to enter their credentials, such as their login and password.
If the user had been using NoPass™, they wouldn’t need to enter their login or password at all. The attacker, who set up the phishing link, say, to a scam version of Confluence and asked for those credentials, would have failed because there would be no need to input any credentials. The user could simply scan a QR code to authenticate.
Since phishing typically relies on stealing credentials through such input, the absence of passwords with NoPass™ (for enterprise clients) or PasswordFree® for customers makes this method ineffective.
Stay tuned for more details on Verizon’s 2024 DBIR
In my next article, I’ll continue with more comments on Verizon's Data Breach Investigations Report, and I’ll elaborate on:
Data breaches 2024 involving a human element (largest category!)
Breaches involving credentials for web applications (always at the top of the chart)
And why you need Desktop Unlock/ PasswordFree® to secure your browser.
P.S.
So far in the article, I mentioned how getting rid of passwords and SMS OTP will protect you against phishing. But authentication requires at least one of three types of authentications:
Something you know (credentials)
Something you have (your device)
Something you are (biometrics)
Here I’m proposing to do away with the first one, something you know. NoPass™ app and PasswordFree® provides “something you have” — which is your phone — but phishing can steal that too.
Add a biometric as your other authentication method with our app and enjoy the highest level of authentication as defined in NIST 800-63-B, AAL3. With our technology, we have you all covered.
Coming soon is my piece on Full Duplex Authentication® — how it gives you all three levels of identity protection and helps fight against phishing, man-in-middle and rogue proxy attacks.
Follow us on LinkedIn to stay updated on our recent posts!





Comments